The top 9 HTTP Request Methods
The top 9 HTTP Request Methods – The World Wide Web is built on the HTTP (Hypertext Transfer Protocol), which is the primary method of data transfer. To request actions to be taken on resources housed on a web server, clients (like web browsers) employ a set of instructions or verbs called HTTP request methods. Every request method has a distinct function and a predetermined behavior.
HTTP Request Structure
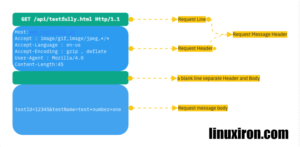
Let’s walk over a typical HTTP request format before diving into different HTTP methods and how to utilize them while creating or using APIs. Every HTTP request must provide a method and a URL (Uniform Resource Locator) or URI (Uniform Resource Identifier) address. The format of the request message that an HTTP client uses to submit an HTTP request to a server is as follows:
- A request-line
- CRLF is followed by zero or more (General Request Entity) header fields.
- The end of the fields is indicated by a blank line (a line with nothing before the CRLF).
- A message-body (optional)
Using HTTP methods for creating Restful APIs
Representational State Transfer, or REST, is an architectural design paradigm for developing online services. RESTful web services are those that adhere to the REST principles. Because they only allow communication between servers located on various computers, these web services are extensively employed by application developers.
Data sharing between clients and servers is made simple through REST. For CRUD activities, REST applications employ HTTP methods like GET, POST, DELETE, PUT, etc.
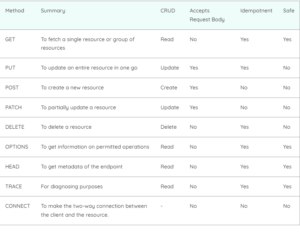
What is a Safe HTTP method?
A safe approach does not modify server data. For instance, the GET and HEAD methods are safe because when a user or program calls them, they do not ask the server to do any side effects.
What is an Idempotent method?
An idempotent method always produces the same result, regardless of how many times it is executed. For instance, this property is shared by the PUT and DELETE procedures. Even if every method that is used in a sequence of requests is idempotent, it is still possible for the sequence to not be idempotent. A set of requests is hence idempotent if the outcome of any one execution of the whole set of requests is always the same.
The most popular HTTP request methods are shown below:
-
GET Method
We send GET Requests to resources like web pages, servers, or APIs when we wish to obtain data from them. For instance, if we want a list of all of our customers or a single customer, we make a GET request to the server.
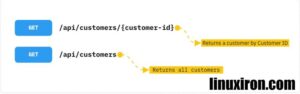
The GET method is regarded as a safe method because it should never modify the data on the resources; instead, it should only read them (read-only). The get method also has idempotence.
How may a GET method be used to test an API?
The GET method is the most often used technique for testing an API. Consequently, we anticipate the following to occur.
- The API returns the 200 Status Code, which implies OK, if the resource is accessible.
- The server frequently sends back a response body in XML or JSON format along with the 200 Status Code. For instance, we anticipate the [GET] /members endpoint to provide a list of members in JSON or XML.
- The 404 Status Code, which denotes Not Found, is returned by the server if it is unable to handle the endpoint.
- When we submit a request with incorrect syntax, the server responds with the 400 Status Code, which signifies “Bad Request.”
-
POST Method
On the backend (server), a new resource is created using the POST method. The data we need is sent to the server in the request body. It is not a secure or irrevocable procedure. Every time we submit a POST request, we don’t anticipate getting the exact same outcome. For instance, two identical POST requests will generate two new, comparable resources with distinct resource ids and the same contents.

We anticipate the following to happen when we submit a POST request to a server:
- The response should ideally include the status code 201, which denotes that a new resource has been created as a result of the POST request on the other side.
- When a POST request is made and no resource is found at the requested URL, the method will return the status code 204, which denotes that there is no content.
A POST endpoint’s test procedure
Testing all POST methods in APIs is strongly advised since the POST method generates data, thus we must be careful while updating data. In addition, remember to remove the generated resource when your testing is complete.
Following are some ideas for testing APIs using POST methods:
- The POST method should be used to create resources, and they should return the 201 Status Code.
- To determine whether the resource was successfully generated, use the GET method. The response should include the newly created resource and you should receive the 200 status code.
- To see if the procedure fails, use inaccurate or improperly structured data when using the POST method.
-
PUT Method
By delivering the updated data to the server as the body of the request using the PUT request method, we may update a resource that already exists. The PUT method replaces a resource’s content when updating it. Use caution while using it since it replaces the entire collection of resources if it applies to a group of resources. Once the existing resource has been successfully changed, the server will return the 200 or 204 status codes.

How may a PUT method be used to test an API?
The PUT method is idempotent and affects all resources, thus we must be sure to do the following actions to test that behavior:
- The server should always respond with the same outcome, no matter how many times you send it a PUT request.
- 200 or 204 status codes should be returned after the server completes the PUT request and changes the resource.
- Make a GET request to verify that the data has been successfully changed on the resource once the server has processed the PUT request.
- The resource must not be modified if the input is invalid or in the incorrect format.
-
PATCH Method
Another seldom used HTTP technique is PATCH. PATCH modifies a resource similarly to PUT, except it only changes some portions of the data. To be more specific, the request [PUT] customers/customerid, for instance, would completely update the data in the Customers entity on the resource. The PATCH technique does, however, update the customer entity’s given data. The usual format for this alteration should generally be XML or JSON.
How may a PATCH method be used to test an API?
Follow the instructions in this article for testing an API using the PUT and POST methods to test it with the PATCH method. Think about the outcomes below:
- Send the server a PATCH request, and it will respond with the HTTP status code 2xx, which denotes that the request has been successfully received, understood, and accepted.
- Make the GET request and ensure that the content has been successfully updated.
- The procedure must fail if the request payload is inaccurate or improperly prepared.
-
DELETE Method
The DELETE method, as its name implies, deletes a resource. No matter how many times it is called, the DELETE method always has the same outcome.
Even if we attempt to remove a deleted resource, the majority of APIs always provide the 200 status code. However, in other APIs, if the target data is no longer available, the method call would return a 404 status code.
How can a DELETE endpoint be tested?
We should use caution while removing items from the server. We are getting rid of important data. Perform the subsequent actions after first confirming that removing data is permissible.
- The POST method should be used to generate new resources. Never use real data while testing DELETE. For instance, try creating a new customer first, then attempting to remove the one you just made.
- Send a DELETE request for the requested resource. A customer with the supplied customer Id is deleted, for instance, when the request [DELETE] /customers/ customer-id is made.
- Use the GET method for the removed customer to retrieve the resource’s status, which should return 404.
With Testfully’s Multi-step tests, you can quickly generate resources to test DELETE endpoints.
-
HEAD Method
The GET technique and the HEAD approach are comparable. However, as it lacks a response body, it must be disregarded if it accidentally returns one. As an illustration, the response body of the [GET] /customers endpoint contains a list of customers. Additionally, [HEAD] /customers accomplish the same thing without returning a list of clients. We can send a HEAD request to find out the size (Content length) of the file or data we are downloading before sending a GET request. The HEAD approach is hence secure and idempotent.
A HEAD endpoint’s test procedure
As long as the API allows it, one benefit of the HEAD method is that we may verify the server’s availability and accessibility. Additionally, since the HEAD method has no response content, it is significantly quicker than the GET method. We anticipate receiving the status code 200 from the API. We may test the API using the HEAD method before using any other HTTP method.
-
OPTIONS Method
Using this technique, we may learn about the server’s permitted HTTP methods for communicating with the specified URL, or we can use an asterisk to refer to the entire server. This procedure is idempotent and secure.
The OPTIONS method is frequently used by several browsers to determine whether or not the requested API restricts CORS (cross-origin resource sharing) operations.
A test procedure for an OPTIONS endpoint
Depending on whether the server accepts the OPTIONS method, we may use the OPTIONS method to test the server for instances of FATAL failure. Think about trying the following.
- Check the header and the returned status code after sending an OPTIONS request.
- Test the failure scenario with a resource that is incompatible with the OPTIONS mechanism.
-
TRACE Method
The TRACE technique is used to make diagnoses. The identical request content that the client previously supplied to the server is used to generate a loop-back test, and a successful response code of 200 OK is returned. The TRACE technique is idempotent and secure.
The TRACE approach could be risky since it might disclose credentials. Using a client-side attack, a hacker might take control of credentials, including internal authentication headers.
How may a TRACE method be used to test an API?
- Make a GET call to /api/status using a regular HTTP request.
- Send it again, replacing GET with TRACE.
- Verify the server’s response. If the information in the response matches that in the first request, the server’s TRACE capability is enabled and operating as intended.
-
CONNECT Method
A client and a server can connect end-to-end using the CONNECT method. It creates a tunnel-like two-way link between them. This technique, for instance, may be used to securely transmit a sizable file from the client to the server.
Comparison of HTTP methods
Browser Support
Only the GET and POST HTTP techniques were supported by early browsers. Today, the majority of contemporary browsers, including IE, Firefox, Safari, Chrome, and Opera, support all common HTTP methods.
Final Thoughts
The foundational system that enables consumers to interact with webpages through browsers is HTTP requests. To facilitate development and testing and guarantee a seamless and straightforward user experience, this framework is also utilized in mobile applications that employ APIs that naturally incorporate combinations of various Request Methods / Verbs.
Learn about the linux commands by clicking the links below
https://linuxiron.com/echo-command-in-linux/
https://linuxiron.com/how-to-use-nice-renice-commands-in-linux/
https://linuxiron.com/how-to-use-kill-commands-in-linux/
https://linuxiron.com/a-beginners-guide-to-htop-for-process-management/
https://linuxiron.com/15-useful-yum-commands-in-linux/
https://linuxiron.com/how-to-use-the-top-command-in-linux/
https://linuxiron.com/17-ps-command-to-monitor-linux-process-with-examples-linuxiron/
https://linuxiron.com/12-cat-commands-in-linux-with-examples/
https://linuxiron.com/archiving-and-compressing-files-and-directories-in-linux/
https://linuxiron.com/how-to-run-the-du-command-in-linux/
https://linuxiron.com/how-to-backup-and-restore-the-linux-system/
-
How many different types of requests exist?
Although the official HTTP Request means registry provides 39 different HTTP verbs, each of which offers a means for effective interactions, API developers often only utilize GET, PUT, or POST. Nine of the more popular ones are reviewed in this article.
-
What techniques are employed in HTTP request messages?
An HTTP method is a verb or word that describes the action to be taken, such as GET, PUT, or POST, or HEAD, or OPTIONS. For instance, the terms GET and POST denotes the need to fetch a resource and push data to the server, respectively (building or changing a resource or producing a temporary document to send back).
-
Which HTTP technique is the safest?
Also permitted is binary data. GET is less secure than POST as the data sent is part of the URL. POST is less secure than GET as it is not saved in browser history or web server logs.
-
What are HTTP and their variations?
The World Wide Web is built on Hypertext Transfer Protocol (HTTP), which is used to transport websites with hypertext links. Designed for data transfer between network devices, HTTP is an application layer protocol that overwrites other network protocol stacks.
-
HTTP request headers: What are they?
The request headers contain additional information about the client making the request as well as the resource that has to be fetched. The response headers contain additional information about the response, such as its location or the server that delivered it.

